Conduktor Gateway Route. Protect. Transform.
An abstraction layer that gives platform teams the Kafka controls they've always wanted - without asking developers to change a single line of code.
Augment Your Infrastructure.
Kafka is powerful, but it wasn't built for everything your organization needs. Gateway adds the capabilities that aren't there natively so you can tailor Kafka to your requirements, not the other way around.
For Platform Teams Scale Kafka across teams without multiplying infrastructure or complexity.
For Security & Compliance Enforce encryption and data policies at the infrastructure layer—not in application code.
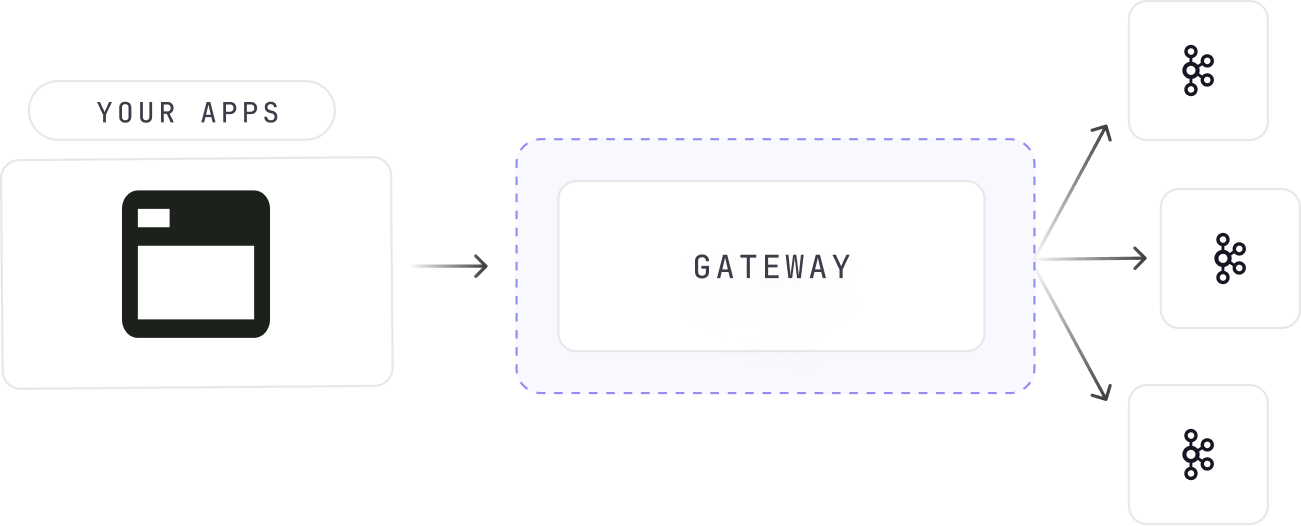
Connect without code changes
Remove network barriers, centralize authentication, and get finer access control than native Kafka ACLs allow.
- Cross-network connectivity without client configuration changes or firewall complexity
- Simplified security management with centralized authentication across hybrid deployments
- Identity-based multi-tenancy enabling secure isolation without separate clusters
- Compliance-ready audit trails meeting SOC2, ISO 27001, and GDPR requirements
# Gateway Configuration
gateway:
environment:
GATEWAY_SECURITY_MODE: GATEWAY_MANAGED
GATEWAY_SECURITY_PROTOCOL: SASL_PLAINTEXT
# OIDC Provider Settings
GATEWAY_OAUTH_JWKS_URL: "https://your-idp.com/.well-known/jwks.json"
GATEWAY_OAUTH_EXPECTED_ISSUER: "https://your-idp.com"
GATEWAY_OAUTH_EXPECTED_AUDIENCES: "kafka-gateway"
GATEWAY_OAUTH_SUB_CLAIM_NAME: "sub"
# Map OIDC identities to Gateway Service Accounts
apiVersion: gateway/v2
kind: GatewayServiceAccount
metadata:
name: my-application
spec:
type: EXTERNAL
externalNames:
- "oauth-subject-id-from-token" # Value from 'sub' claim in JWT// Audit log event
{
"id": "f47ac10b-58cc-4372-a567-0e02b2c3d479",
"type": "APIKEYS_REQUEST",
"time": "2024-10-15T14:30:45.123Z",
"source": "//kafka/cluster/production",
"authenticationPrincipal": "tenant-acme",
"userName": "order-service",
"connection": {
"localAddress": "172.17.0.2:6969",
"remoteAddress": "192.168.1.42:52341"
},
"eventData": {
"apiKeys": "PRODUCE",
"topics": [
{ "name": "orders", "partition": 0 },
{ "name": "orders", "partition": 1 }
]
},
"specVersion": "0.1.0"
}Migrate and test resilience safely
Execute infrastructure changes confidently while applications continue running unchanged.
- Zero-downtime migrations switching clusters without application config changes or team coordination
- Seamless failover maintaining continuity when infrastructure fails
- Safe resilience testing injecting latency, errors, and corruption without production risk
# Gateway cluster configuration
config:
main:
bootstrap.servers: kafka-primary:9092
security.protocol: SASL_SSL
sasl.mechanism: PLAIN
failover:
bootstrap.servers: kafka-secondary:9092
gateway.roles: failover
# Switch from main → failover
curl -X POST 'http://localhost:8888/gateway/v2/cluster-switching' \
-H 'Content-Type: application/json' \
-d '{"fromPhysicalCluster": "main", "toPhysicalCluster": "failover"}'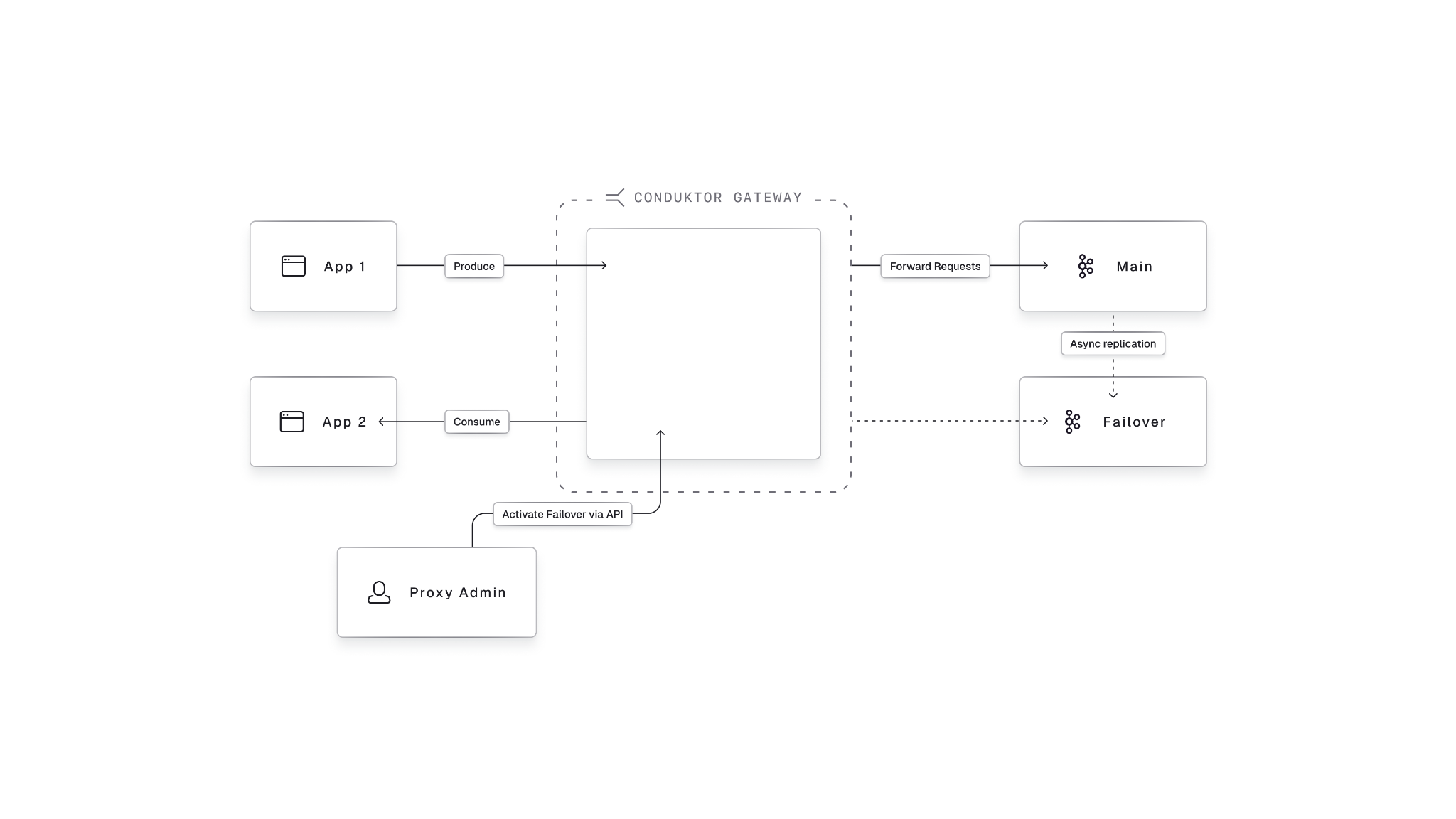
# Chaos testing interceptor
apiVersion: gateway/v2
kind: Interceptor
metadata:
name: chaos-broken-broker
spec:
pluginClass: io.conduktor.gateway.interceptor.chaos.SimulateBrokenBrokersPlugin
priority: 100
config:
rateInPercent: 100
errorMap:
FETCH: UNKNOWN_SERVER_ERROR
PRODUCE: CORRUPT_MESSAGEDecouple tenants from clusters
Serve multiple teams from shared infrastructure with independent namespaces and naming conventions.
- Lower infrastructure costs through cluster consolidation with isolated logical environments per team
- 90%+ partition reduction by concentrating low-volume topics and lowering broker overhead
- Rename topics transparently without client changes or exposing internal naming to consumers
apiVersion: gateway/v2
kind: VirtualCluster
metadata:
name: payments-team
spec:
type: Standard
aclEnabled: true
superUsers:
- payments-admin
apiVersion: gateway/v2
kind: VirtualCluster
metadata:
name: orders-team
spec:
type: Standard
aclEnabled: true
superUsers:
- orders-admin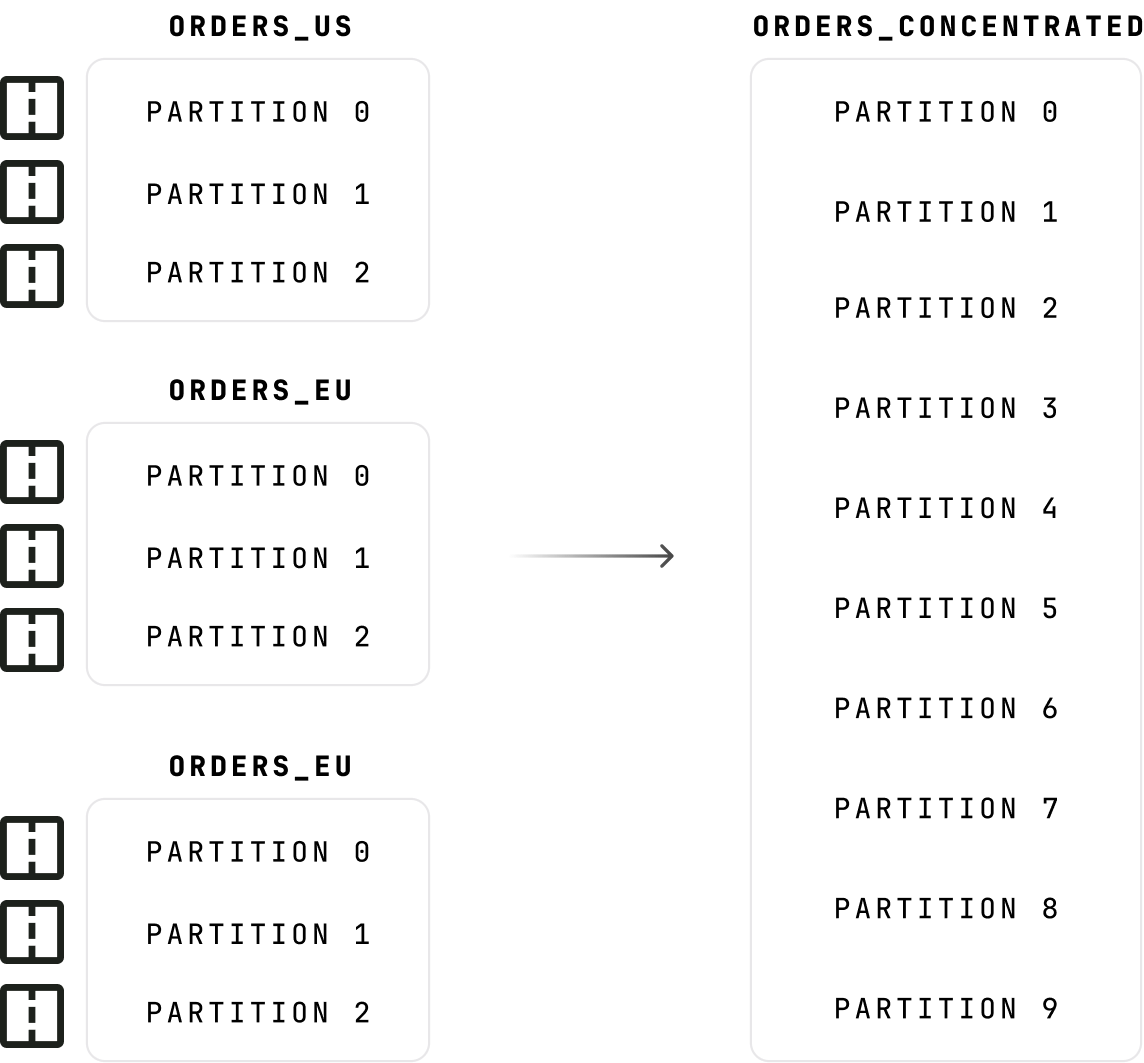
apiVersion: gateway/v2
kind: AliasTopic
metadata:
name: customers
vCluster: partner-team
spec:
physicalName: internal-crm-customers
apiVersion: gateway/v2
kind: AliasTopic
metadata:
name: orders
vCluster: partner-team
spec:
physicalName: internal-billing-ordersHandle load efficiently
Lighten broker load and serve filtered topic views without duplicating data or adding infrastructure.
- Filtered views without duplication using SQL-based projections instead of stream processing pipelines
- Faster high-frequency reads by caching messages and reducing broker load
- Transparent large payload handling offloading oversized messages to S3 or Azure Blob automatically
apiVersion: gateway/v2
kind: Interceptor
metadata:
name: sql-filter-adults
spec:
pluginClass: io.conduktor.gateway.interceptor.VirtualSqlTopicPlugin
priority: 100
config:
virtualTopic: customers-adult
statement: |
SELECT firstName, lastName, email, country
FROM customers
WHERE age >= 18 AND country = 'US'
schemaRegistryConfig:
host: http://schema-registry:8081apiVersion: gateway/v2
kind: Interceptor
metadata:
name: cache-high-traffic-topics
spec:
pluginClass: io.conduktor.gateway.interceptor.CacheInterceptorPlugin
priority: 100
config:
topic: "events.*"
cacheConfig:
type: IN_MEMORY
inMemConfig:
cacheSize: 1000
expireTimeMs: 60000apiVersion: gateway/v2
kind: Interceptor
metadata:
name: offload-large-messages-s3
spec:
pluginClass: io.conduktor.gateway.interceptor.LargeMessageHandlingPlugin
priority: 100
config:
topic: "media.*"
minimumSizeInBytes: 1048576
localDiskDirectory: /tmp/kafka-offload
s3Config:
bucketName: kafka-large-messages
region: us-east-1Prevent misconfigurations
Enforce organizational standards and prevent destabilizing changes before they reach production.
- Prevent production issues by enforcing data contracts and config standards before deployment
- Eliminate noisy neighbors with bandwidth and rate limits per tenant or cluster
- Enforce best practices ensuring acks, compression, and idempotence across all producers
- Control metadata centrally transforming headers without application changes
apiVersion: gateway/v2
kind: Interceptor
metadata:
name: topic-governance-policy
spec:
pluginClass: io.conduktor.gateway.interceptor.safeguard.CreateTopicPolicyPlugin
priority: 100
config:
namingConvention:
value: "^[a-z]+-[a-z]+-[a-z]+$"
action: BLOCK
numPartition:
min: 3
max: 12
action: OVERRIDE
overrideValue: 6
replicationFactor:
min: 3
max: 3
action: BLOCK
retentionMs:
min: 86400000
max: 604800000
action: OVERRIDE
overrideValue: 259200000apiVersion: gateway/v2
kind: Interceptor
metadata:
name: producer-rate-limit
scope:
vCluster: payments-team
spec:
pluginClass: io.conduktor.gateway.interceptor.safeguard.ProducerRateLimitingPolicyPlugin
priority: 100
config:
maximumBytesPerSecond: 10485760
action: BLOCK
apiVersion: gateway/v2
kind: Interceptor
metadata:
name: consumer-rate-limit
scope:
vCluster: payments-team
spec:
pluginClass: io.conduktor.gateway.interceptor.safeguard.ConsumerRateLimitingPolicyPlugin
priority: 100
config:
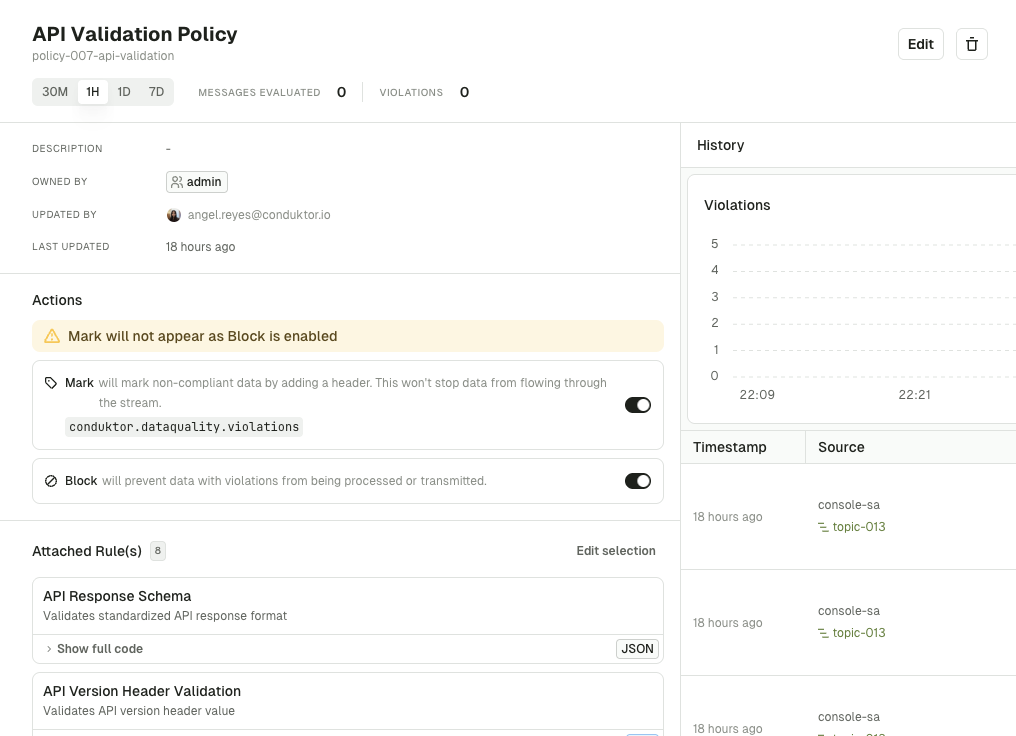
maximumBytesPerSecond: 52428800Stop bad data at the source
Validate data as it flows through—not after it's caused problems downstream.
- Detect degradation early by evaluating messages against validation rules in real-time
- Block bad data from entering Kafka by enforcing quality rules at the source
- Eliminate consumer failures by ensuring only valid data reaches downstream systems
{
"name": "myDataQualityProducerPlugin",
"pluginClass": "io.conduktor.gateway.interceptor.safeguard.DataQualityProducerPlugin",
"priority": 100,
"config": {
"statement": "SELECT x FROM orders WHERE amount_cents > 0 AND amount_cents < 1000000",
"schemaRegistryConfig": {
"host": "http://schema-registry:8081"
},
"action": "BLOCK_WHOLE_BATCH",
"deadLetterTopic": "dead-letter-topic",
"addErrorHeader": false
}
}
Encrypt consistently across apps
Define encryption once and apply it uniformly, without touching application code.
- Prevent config drift with centralized encryption and standardized KMS connections
- Meet compliance requirements integrating with Vault, AWS KMS, Azure Key Vault, GCP KMS, or Fortanix
- Protect fields selectively encrypting sensitive data while keeping the rest readable
- Enable analytics on protected data using tokenization that preserves format without exposing values
apiVersion: gateway/v2
kind: Interceptor
metadata:
name: encrypt-pii-fields
spec:
pluginClass: io.conduktor.gateway.interceptor.EncryptPlugin
priority: 100
config:
topic: "customers.*"
recordValue:
fields:
- fieldName: ssn
keySecretId: "vault-kms://vault:8200/transit/keys/pii-key"
algorithm: AES256_GCM
- fieldName: creditCard.number
keySecretId: "vault-kms://vault:8200/transit/keys/payment-key"
algorithm: AES256_GCM
- fieldName: email
keySecretId: "in-memory-kms://email-key"
algorithm: AES128_GCM
kmsConfig:
vault:
uri: http://vault:8200
type: TOKEN
token: ${VAULT_TOKEN}apiVersion: gateway/v2
kind: Interceptor
metadata:
name: encrypt-with-kms
spec:
pluginClass: io.conduktor.gateway.interceptor.EncryptPlugin
priority: 100
config:
topic: ".*"
recordValue:
fields:
- fieldName: ssn
keySecretId: "vault-kms://..."
- fieldName: payment.cardNumber
keySecretId: "aws-kms://..."
- fieldName: healthRecord
keySecretId: "azure-kms://..."
kmsConfig:
vault:
uri: http://vault:8200
type: APP_ROLE
aws:
basicCredentials:
accessKey: ${AWS_ACCESS_KEY}
azure:
tokenCredential:
tenantId: ${AZURE_TENANT_ID}Share data securely
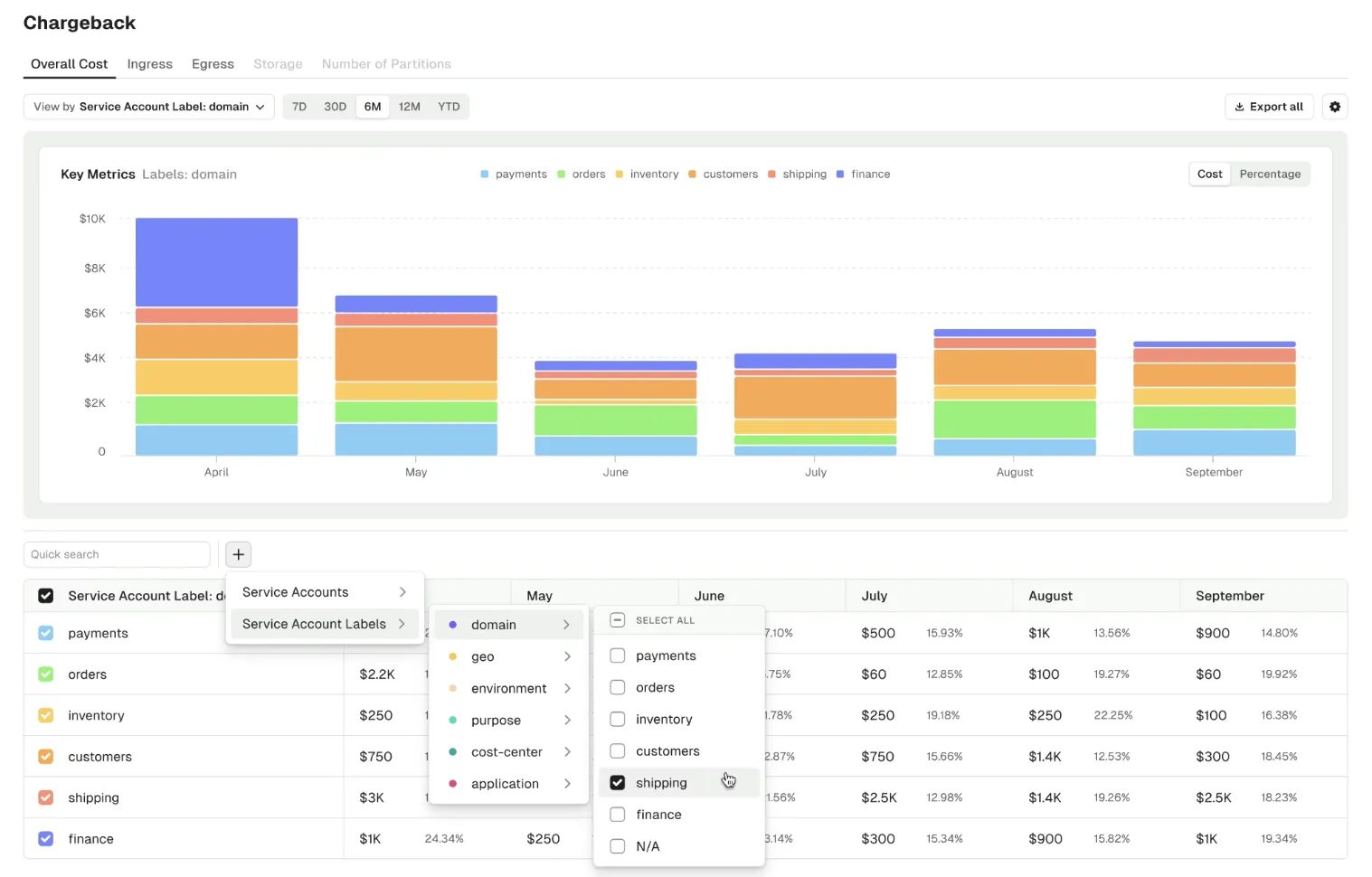
Give partners access to the data they need without exposing your full cluster or duplicating pipelines.
- Control external access through isolated virtual clusters with topic mappings and rate limits
- Share without duplication using topic views tailored for partner-specific access
- Adapt formats automatically transforming data for external consumption without dual-write patterns
- Track usage for billing with consumption metrics that enable cost allocation and chargeback
apiVersion: gateway/v2
kind: VirtualCluster
metadata:
name: partner-a
spec:
type: Partner
aclEnabled: true
superUsers:
- partner-admin
apiVersion: gateway/v2
kind: GatewayServiceAccount
metadata:
name: partner-admin
vCluster: partner-a
spec:
type: LOCAL
apiVersion: gateway/v2
kind: AliasTopic
metadata:
name: orders
vCluster: partner-a
spec:
physicalName: internal-ordersMeasurable Impact
Real results from platform teams using Gateway.
European airline moved to Confluent Cloud in 9 months with zero downtime.
Payment processor achieved MasterCard and VISA certification with Gateway encryption.
FlixBus scaled multi-tenancy without multiplying infrastructure.
Encryption, routing, and policies applied at the proxy layer—not in applications.
Read more customer stories
Ready to Try Gateway?
See how platform teams use Gateway to add encryption, multi-tenancy, and traffic control to their Kafka clusters without changing application code.